So this is last part of this series. Hopefully, I don’t need to write another post.
From previous post, I discussed about how to install and configure Trend Deep Security 7.5 on vSheild. This post will talk little bit more about configuration and performance review.
In my last post, I have installed vShield Zone on host, Install DS Manager one of my VMs which is also vCenter, and push DS Virtual Appliance on to one of hosts.
Then, I changed the IP and network configuration on the DS VA and activate it with Deep Security Virtual Appliance.
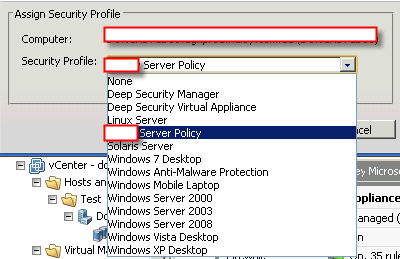
Please be aware that Security Policy is playing an important role in the DS. You need to make sure all protected VMs having correct Security Policy.
Once you finished the VA, we can go back to DS manager and take a quick look.
I would like to list some common issues you may encounter.
If anti-Malware status is not Capable, it means vEndpoint is not installed on this ESX host.
If Anti-Malware is on, but the color is blue. It means you haven’t assigned correct policy on this VM. In default, there is no policy at all. Just right click the VM and follow the instruction.
You better actually create your own policy before you apply. Some default policy(like windows 2k3) doesn’t have all protection on and doesn’t allow certain protocol (e.g: RDP). The best way is to make copy of old policy and customize a new one for yourself.
The next step is to prepare your VMs. All what you need to do is to install vShield Driver agent and DS Agent. Once you finish installation, you must reactivate your vm from DS Manager to let DS Manager to check VM status.
If you have installed both agents and apply right policy, reactivate your vm from DS Manager. You should see something like this in the DS Manager.
It should have all greens and Agent should running. Your VM should be protected at each level from crossing both Appliance(working with vEndpoint) and Agent.
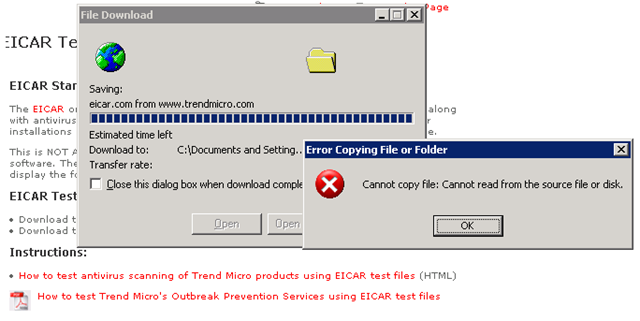
One more thing when you try to install DS Agent, you need to copy the installation on local disk of VM and install. Otherwise, you will encounter this error.
Virus download test
I have a protected VM which has all features turned on. Let’s see how it react when I tried to download a virus sample file from Internet.
It actually worked!
Does Deep Security actually reduce resource consumption?
Here is the big question. The reason we spent so much time to deploy this product is the rumour that it can save the resource comparing with traditional AV solution. Let’s take a look.
I installed OfficeScan on one of test machines. I monitored the resource which has been consumed from CPU, Memory,DISK,Network for both test VM and Host as base line. I will scan a vm with officescan once. And also scan it with DS.
Protected VM CPU
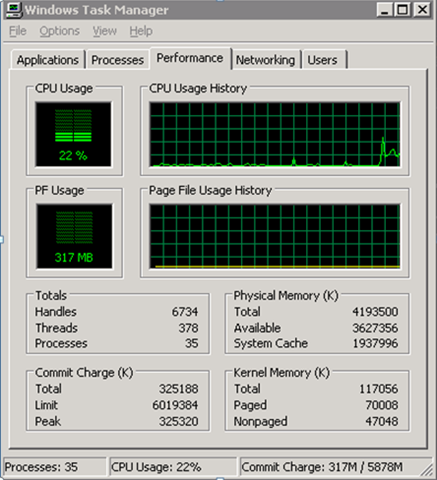
Protected VM CPU with OfficeScan
CPU: 50% of one core. It lasts 10 mins.
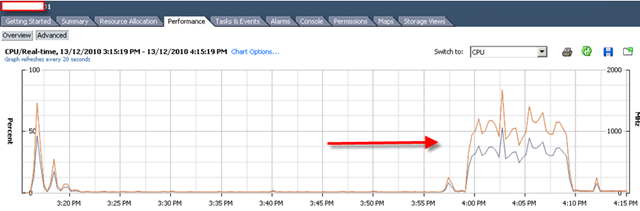
Protected VM CPU with DS
only 22% on CPU comparing with 50% on Office Scan.
Note: I ran twice on this test.
Protected VM DISK
Protected VM disk with OfficeScan
Disk: 5000KBps for 10 mins.
Protected VM disk with DS:
It’s very interesting to see the first run disk but nothing on second. The reason is the first run has already load disk data into memory and it doesn’t require to load again at second time. It proves DS is load to memory and scan only memory theory. The DS scan finished in 4.5 mins.
Protected VM Memory
Protected VM with OfficeScan
Memory: Consumed memory is 1.25GB, and active memory is 4GB.
Protected VM with DS
50% of active memory in 4.5 mins. I ran twice.
Protected VM Network
Protected VM with OfficeScan
Network: OfficeScan tried to contact OfficeScan server at beginning. Then, it went quiet.
Protected VM Network Activity with DS:
There is almost nothing on network. It means DS is using ESX module to scan memory directly. It doesn’t go through normal network channel. Because it is using similar theory as vSwitch, I call it a protected vSwitch channel.
From what I can see via Protected VM angle, the resource has been consumed almost 50% less and use only half time to finish scan.
Because using DA actually involves to use Deep Security Virtual Appliance to scan. We need to take look about DS VA.
DS VA CPU:
The truth behind scene is DS VA is actually scanning the data instead of protected VM. That’s why you see low utilization on VM because all what it did was to load data into memory and call vShield Endpoint driver to let DS VA to scan.
DS VA Disk:
Almost nothing on disk VA disk activity.
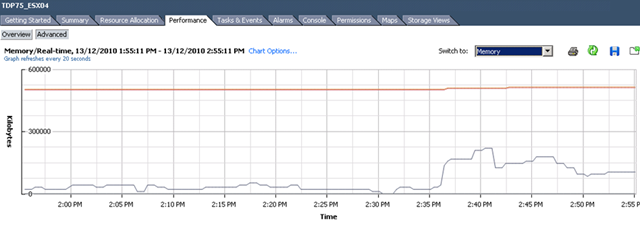
DS VA Memory:
It consume 1.5GB memory on VA. It’s understandable.
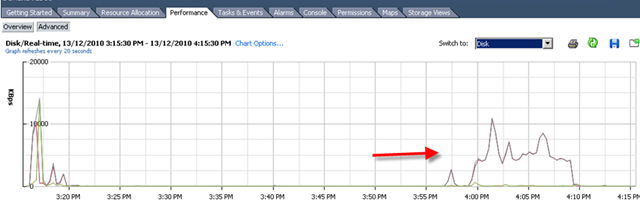
DS VA Network:
This is very interesting. According to this chart, the network activity on DS VA is very high during scanning. It means vShield Endpoint will open port for all VMs sitting on that protected vSwitch instead of just DS VA.
This is the vSwitch vShield Endpoint use. It’s just normal vSwith and you can add adapters if you want. It does bring my concern whether this could be potential security breach.
Here is moment of truth. Will DS actually save resource from ESX perspective?
Following is the data from Physical ESX Host:
ESX CPU utilization
ESX CPU with OfficeScan
4% of total CPUs on ESX box. I have nothing else was running on that host.
ESX Host CPU Performance on DS
It does finish scan in half time but it actually use 6% of CPUs. Be aware this is not including overhead of ESX host CPU. It’s 2% of higher than OfficeScan.
ESX Disk with OfficeScan
Disk activity on ESX host.
ESX Disk activity with DS
It’s same disk activity but with half loading time.
There ain’t much point to check memory since everything is happening in the memory. Just one module to scan another chunk of memory in the host. That’s all.
Conclusion:
Let’s sum up with what we have learned from those data. Please be aware I’m only test single machine scan.
Resource consumption:
ESX Host
| OfficeScan | DS 7.5 | ||
| CPU Util | 4% | 6% | |
| CPU Used time | 10 mins | 4.5 mins | |
| DISK Util | 200CMD/s | 200CMD/s | |
| DISK Used time | 10 mins | 4.5 mins | |
| Memory | Same | Same | |
| Network | 0 | 0 | Nothing on pNIC |
It does seem like Host CPU is consumed more resource than officeScan.
but It seems that DS VA doesn’t support multiple threads scanning at same time. If that’s the case, a host can hold about 30 VMs max. So DS Manager will schedule to scan all machines in different time.
This is the end of this Session of this year!
I wish everyone has a wonderful Christmas and Happy New Year!!





















5 Comments
How do you vmotion a DSVA? I tried and cannot. If I cannot evacuate a DSVA from a host, how can I put it into maintenence mode for patching?
I guess you can power off the DSVA. At the end, it’s just a VM.
This is pretty interesting, but it misses the real point.
If you are to run 1 machine, don’t make it virtual. If you’re using ESX, it means you have multiple VMs, or even a few View servers and hundreds of User VMs. That’s where you need Deep Security. Thus, you ought to compare multiple machines running OfficeScan to multiple machines running Deep Security, and then you get the point, the overhead per VM is increasing linear with OS, while increasing log with DS, that’s all the idea.
Regarding the question of vMotion’ing a DSVA, the DSVA is locked to it’s ESX and won’t move (Hopefully! It’s connected to the local ESX’s vShield Loadable Kernel Module…). To go to maintenance, expurge the ESX from all other VMs, shutdown the DSVA, go to maintenance mode, do what you have to do (updates?), exit mainenance mode, start the DSVA, move back the VMs (DRS may do it by itself at some stage).
Hello, have you tested with Officescan conventional Scanning mode or with smart scan?
“VMware vShield Endpoint and Trend Micro Deep Security 7.
5 understanding Part 3 | GeekSilver’s Blog” definitely got myself addicted on ur internet page! I actuallydefinitely will wind up being back a lot more often. Thank you -Jamison
3 Trackbacks/Pingbacks
[…] VMware vSphere vShield 4.1 Understanding Part 1 VMware vShield Endpoint and Trend Micro Deep Security 7.5 understanding Part 2 VMware vShield Endpoint and Trend Micro Deep Security 7.5 understanding Part 3 […]
[…] VMware vSphere vShield 4.1 Understanding Part 1 VMware vShield Endpoint and Trend Micro Deep Security 7.5 understanding Part 2 VMware vShield Endpoint and Trend Micro Deep Security 7.5 understanding Part 3 […]
[…] VMware vShield Endpoint and Trend Micro Deep Security 7.5 understanding Part 2 (GeekSilver) VMware vShield Endpoint and Trend Micro Deep Security 7.5 understanding Part 3 (GeekSilver) VMware vSphere vShield 1.0 design flaw with vCenter as VM? (GeekSilver) VMware vShield […]